RITSEC CTF 2021 notes
RITSEC CTF 2021 is a security-focused competition that features the following categories: Bin, OSINT, PWN, Crypto, Forensics, Steganography, and Web. We welcome beginners and more advanced security friends! There will be three brackets: RIT students, other college students, and everyone else.
1. snek [rev/bin]
The challenge statement:
No step on snek
Author: knif3
File: snek
$ file snek # what is it?
snek: python 3.7 byte-compiled
Google: “decompile python 3.7 byte compiled” => https://pypi.org/project/uncompyle6/
$ uncompyle6 snek
# file snek
# path snek must point to a Python source that can be compiled, or Python bytecode (.pyc, .pyo)
$ mv snek snek.pyc && uncompyle6 snek.pyc # rename it and try again.
# uncompyle6 ...
"""
Written for RITSEC CTF 2021
Author: knif3
Flag: RITSEC{}
TODO: Finish this challenge
"""
class d(object):
def __init__(self, password):
self.password = password.encode()
self.decrypt = [97, 98, 99, 100, 101, 102, 103, 104, 105, 106, 107, 108, 109, 110, 111, 112, 113, 114, 115, 116, 117, 118, 119, 120, 121, 122, 65, 66, 67, 68, 69, 70, 71, 72, 73, 74, 75, 76, 77, 78, 79, 80, 81, 82, 83, 84, 85, 86, 87, 88, 89, 90, 95, 82, 83, 123, 97, 108, 108, 95, 104, 105, 36, 36, 95, 97, 110, 100, 95, 110, 48, 95, 98, 105, 116, 51, 125]
def __eq__(self, other):
if self.password == bytes(self.decrypt):
print('!flag')
return True
return False
x = input('Enter my name: ')
a = d(x)
if a == x:
print('IS_THIS_THE_FLAG??')
print('NOPE')
else:
print('WRONG')
$ python3
>>> "".join([chr(i) for i in [97, 98, 99, 100, 101, 102, 103, 104, 105, 106, 107, 108, 109, 110, 111, 112, 113, 114, 115, 116, 117, 118, 119, 120, 121, 122, 65, 66, 67, 68, 69, 70, 71, 72, 73, 74, 75, 76, 77, 78, 79, 80, 81, 82, 83, 84, 85, 86, 87, 88, 89, 90, 95, 82, 83, 123, 97, 108, 108, 95, 104, 105, 36, 36, 95, 97, 110, 100, 95, 110, 48, 95, 98, 105, 116, 51, 125]])
'abcdefghijklmnopqrstuvwxyzABCDEFGHIJKLMNOPQRSTUVWXYZ_RS{all_hi$$_and_n0_bit3}'
2. DababyWeb [web]
The challenge statement:
Dababy wanted to share a message, but he seemed to put it too high up…
34.72.118.158:6284
Author: Darkfowl
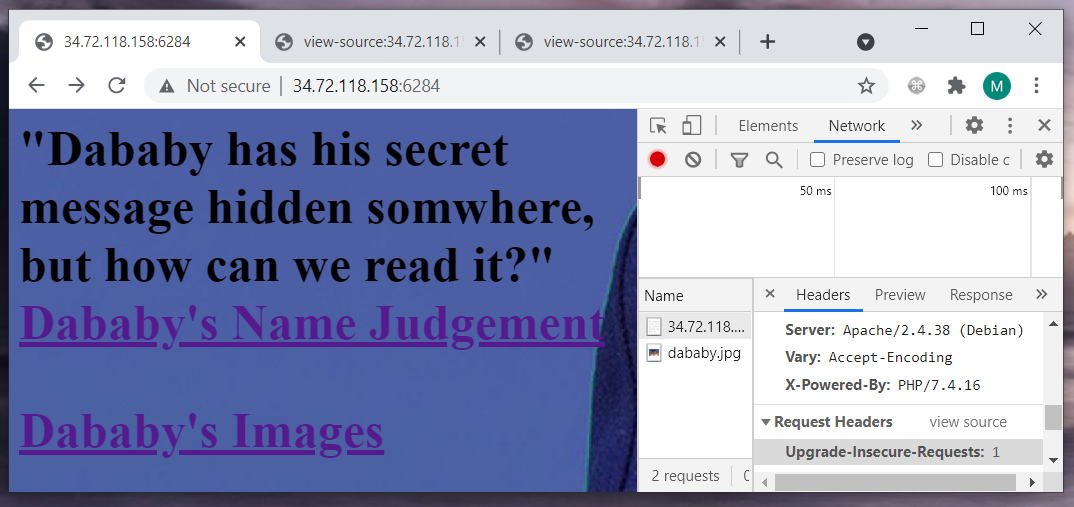
 Google: “PHP local file inclusion cheat sheet” => https://highon.coffee/blog/lfi-cheat-sheet/. Am I feeling lucky?
Google: “PHP local file inclusion cheat sheet” => https://highon.coffee/blog/lfi-cheat-sheet/. Am I feeling lucky? file=./flag.txt => no, file=./../flag.txt. => yes RS{J3TS0N_M4D3_4N0TH3R_0N3}. The proper solution seems to be published here.
3. Robots [web]
The challenge statement:
Robots are taking over. Find out more.
34.69.61.54:5247
Author: f1rehaz4rd
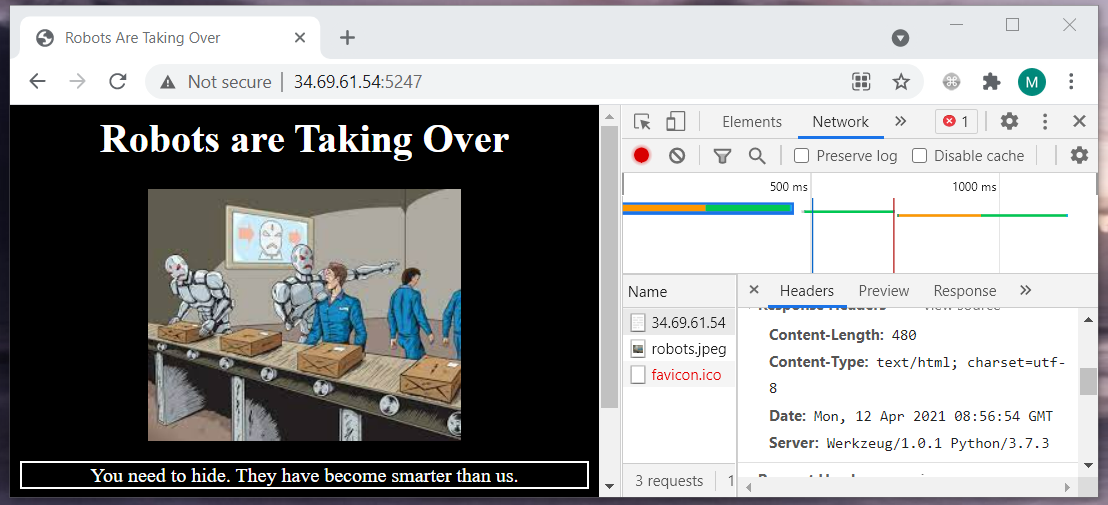
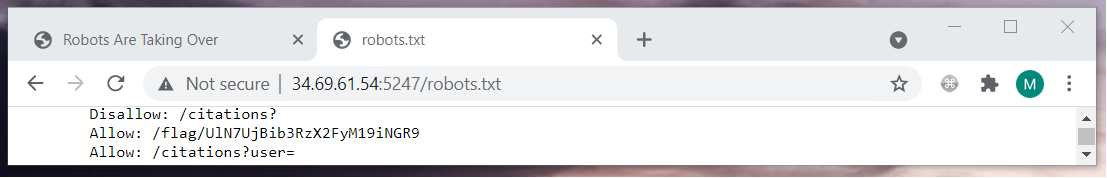
$ echo UlN7UjBib3RzX2FyM19iNGR9 | base64 -d
RS{R0bots_ar3_b4d}
4. Sessions [web]
The challenge statement:
Find the flag.
http://34.69.61.54:4777
Author: f1rehaz4rd
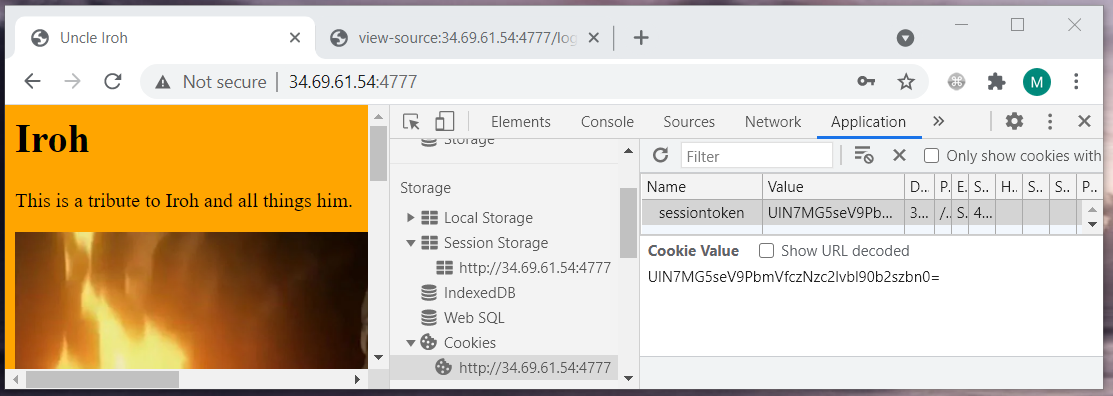
$ echo UlN7MG5seV9PbmVfczNzc2lvbl90b2szbn0= | base64 -d
RS{0nly_One_s3ssion_tok3n}
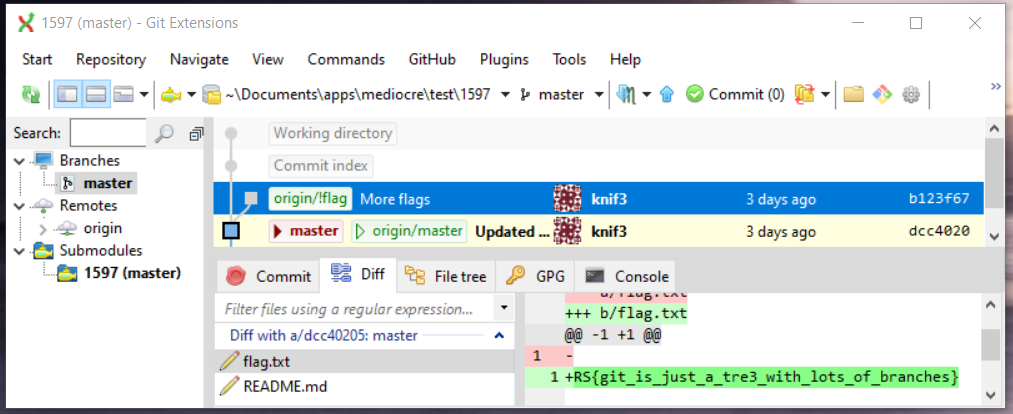
5. 1597 [forensics]
The challenge statement:
… as in https://xkcd.com/1597/
http://git.ritsec.club:7000/1597.git/
Author: knif3
git clone http://git.ritsec.club:7000/1597.git/
6. Inception CTF: Dream 1 [forensics]
The challenge statement:
The purpose of this CTF challenge is to identify common methods of hiding malicious files and code. In most cases adversaries will attempt
to evade defenses in many cases by masquerading, hiding files, and more. There are five directories like the five levels in the movie
Inception: Reality - Van Chase - The Hotel - Snow Fortress - Limbo. You will find one flag in each of the levels, that flag will also
be the password to extract the next directory. Requirements: • You must have 7zip installed • Drop the InceptionCTF.7z on the Desktop as “InceptionCTF” • Use the option “Extract to “name of directory” for the CTF to function properly Missing either of the above may result
in complications which may cause issues when attempting to find flags. NOTE: The flag format isRITSEC{}
Dream 1: We have to get to their subconscious first, look for a hidden text file within the directory “Reality” this flag will unlock the next.
We would like to thank our sponsor @SRA for contributing this challenge!
File: InceptionCTFRITSEC.7z
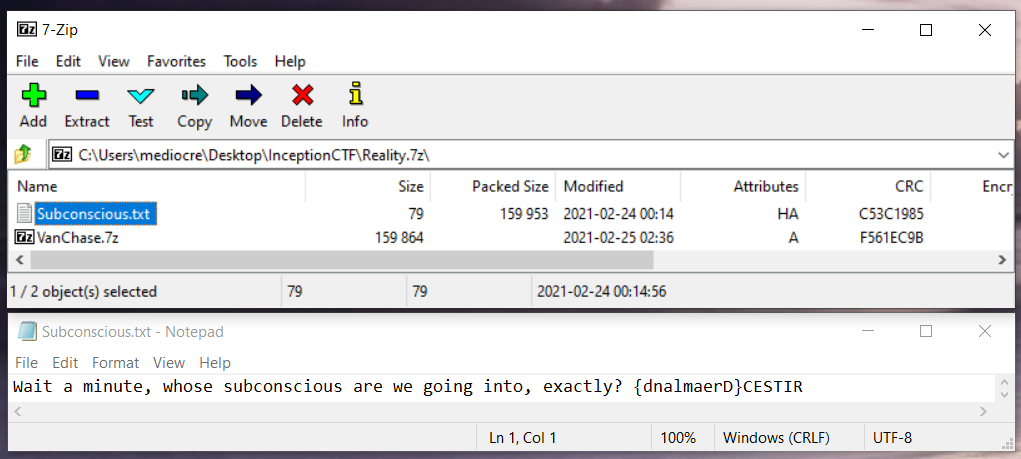
# reverse the string with python3
$ python3 -c 'print("{dnalmaerD}CESTIR"[::-1])'
RITSEC}Dreamland{
# change directory
> cd Desktop\InceptionCTF
# make 7z runnable from cmd
> set PATH=%PATH%;C:\Program Files\7-Zip\
# extract `Reality.7z` to `Reality` folder
> 7z e Reality.7z -oReality
7-Zip 19.00 (x64) : Copyright (c) 1999-2018 Igor Pavlov : 2019-02-21 ...
Extracting archive: Reality.7z, Everything is Ok, Files: 2 ...
# change dir to `Reality`
> cd Reality
# extract `VanChase.7z` to `VanChase` folder using `Dreamland` password.
> 7z e VanChase.7z -oVanChase -pDreamland
7-Zip 19.00 (x64) : Copyright (c) 1999-2018 Igor Pavlov : 2019-02-21 ...
Extracting archive: VanChase.7z, Everything is Ok, Files: 3 ...
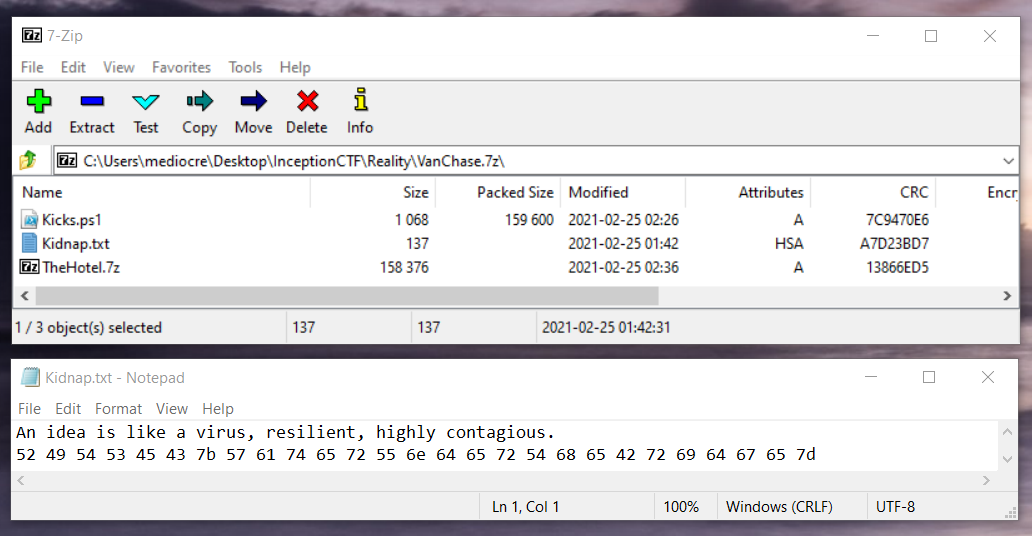
$ python3
>>> bytes.fromhex('52 49 54 53 45 43 7b 57 61 74 65 72 55 6e 64 65 72 54 68 65 42 72 69 64 67 65 7d').decode()
RITSEC{WaterUnderTheBridge}
# set the correct password for the `VanChase\Kick.ps1` script.
set-alias laylow "$env:ProgramFiles\7-Zip\7z.exe"
$7zf = "TheHotel.7z"
$7zp = "WaterUnderTheBridge" # <---- Enter Password inbetween the Double Qoutes
$7zo = "-aoa"
laylow x $7zf "-p$7zp" $7zo
Start-Sleep -s 3
New-Item -Path $env:userprofile\Desktop\InceptionCTF\Reality\VanChase\ -Name TheHotel -ItemType "directory"
Start-Sleep -s 3
Move-Item -Path $env:userprofile\Desktop\InceptionCTF\Reality\VanChase\ThePointMan.txt -Destination $env:userprofile\Desktop\InceptionCTF\Reality\VanChase\TheHotel\ThePointMan.txt
Move-Item -Path $env:userprofile\Desktop\InceptionCTF\Reality\VanChase\ -Destination $env:userprofile\Desktop\InceptionCTF\Reality\VanChase\TheHotel\
Move-Item -Path $env:userprofile\Desktop\InceptionCTF\Reality\VanChase\SnowFortress.7z -Destination $env:userprofile\Desktop\InceptionCTF\Reality\VanChase\TheHotel\SnowFortress.7z
Start-Sleep -s 3
cd $env:userprofile\Desktop\InceptionCTF\Reality\VanChase\TheHotel\ | cmd.exe --% /c type > ThePointMan.txt:
Remove-Item -Path $env:userprofile\Desktop\InceptionCTF\Reality\VanChase\TheHotel\
# change dir to `Vanchase`
> cd VanChase
# run the `Kick.ps1` script
> powershell -executionpolicy bypass -File .\Kicks.ps1
7-Zip 19.00 (x64) : Copyright (c) 1999-2018 Igor Pavlov : 2019-02-21 ...
Extracting archive: VanChase.7z, Everything is Ok, Files: 3 ...
The content of the TheHotel\ThePointMan.txt
Q3JlYXRlIGEgbWF6ZSBpbiB0d28gbWludXRlcyB0aGF0IHRha2VzIG1lIG9uZSBtdW5pdGUgdG8gc29sdmUuIA==
59 6f 75 27 72 65 20 77 61 69 74 69 6e 67 20 66 6f 72 20 61 20 74 72 61 69 6e 2c 20 61 20 74 72 61 69 6e 20 74 68 61 74 20 77 69 6c 6c 20 74 61 6b 65 20 79 6f 75 20 66 61 72 20 61 77 61 79 2e 20 59 6f 75 20 6b 6e 6f 77 20 77 68 65 72 65 20 79 6f 75 20 68 6f 70 65 20 74 68 69 73 20 74 72 61 69 6e 20 77 69 6c 6c 20 74 61 6b 65 20 79 6f 75 2c 20 62 75 74 20 79 6f 75 20 63 61 6e 27 74 20 62 65 20 73 75 72 65 2e 20 62 75 74 20 69 74 20 64 6f 65 73 6e 27 74 20 6d 61 74 74 65 72 20 2d 20 62 65 63 61 75 73 65 20 77 65 27 6c 6c 20 62 65 20 74 6f 67 65 74 68 65 72 2e 20
|[email protected]@DH.GLBB@W .aDWILKB. BXOR 25
Gung znal qernzf jvguva qernzf vf gbb hafgnoyr!
--. ..- .-.
..-. .-. .-. --.-
--. ..- -. --.
.--- .-.
-.-. -.-- -. .- --. .-. --.-
...- .-
--. ..- ...- ..-.
--.. -. .- .----. ..-.
--.. ...- .- --.-
--.. -. .-..
.--. ..- -. .- - .-.
.-. .. .-. . .-.. --. ..- ...- .- - .-.-.-
No place for a tourist in this job.
I tried to decode all of these, soon I realized there was no point in that. I think the author may or may not have trolled us.
$ echo NTIgNDkgNTQgNTMgNDUgNDMgN2IgNDYgNDAgMjEgMjEgNjkgNmUgNjcgNDUgNmMgNjUgNzYgNDAgNzQgNmYgNzIgN2Q= | base64 -d
52 49 54 53 45 43 7b 46 40 21 21 69 6e 67 45 6c 65 76 40 74 6f 72 7d
$ python3
>>> bytes.fromhex('52 49 54 53 45 43 7b 46 40 21 21 69 6e 67 45 6c 65 76 40 74 6f 72 7d').decode()
RITSEC{F@!!ingElev@tor}
# change dir to `TheHotel` folder
> cd TheHotel
# extract `SnowFortress.7z` to `SnowFortress` folder using `F@!!ingElev@tor` password.
> 7z e SnowFortress.7z -oSnowFortress -pF@!!ingElev@tor
7-Zip 19.00 (x64) : Copyright (c) 1999-2018 Igor Pavlov : 2019-02-21 ...
Extracting archive: VanChase.7z, Everything is Ok, Files: 2 ...
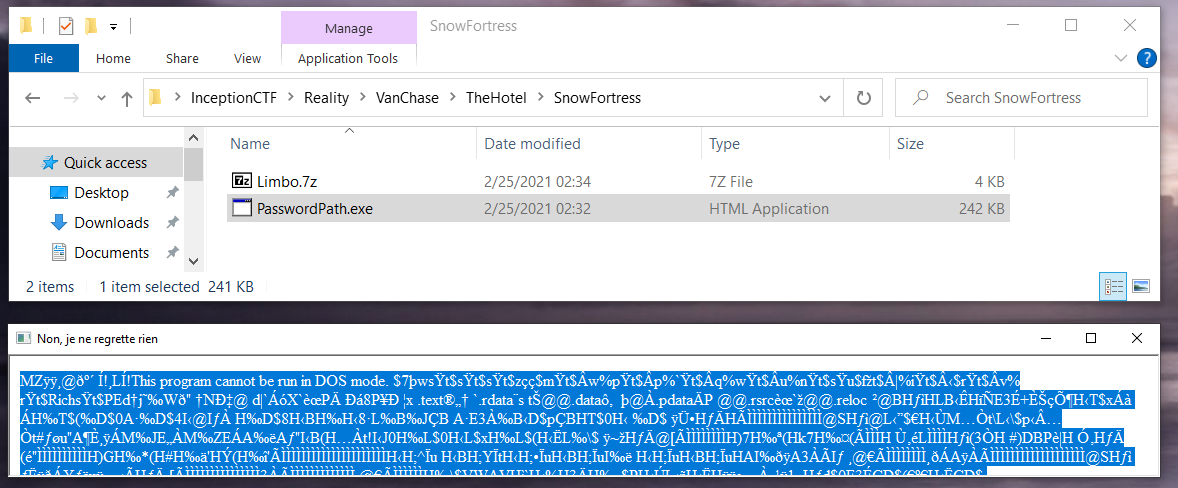
This app seems to display a lot of gibberish text mostly. But the bottom part of it has few interesting lines.
...
Building Dreams....
-.. .-. . .- -- ... ..-. . . .-.. .-. . .- .-.. .-- .... . -. .-- . .----. .-. . .. -. - .... . -- .-.-.-
.. - .----. ... --- -. .-.. -.-- .-- .... . -. .-- . .-- .- -.- . ..- .--. - .... .- - .-- . .-. . .- .-..
.. --.. . ... --- -- . - .... .. -. --. .-- .- ... .- -.-. - ..- .- .-.. .-.. -.-- ... - .-. .- -. --. .
.-.-.- .-. .. - ... . -.-. -...- -.. .. ...- . .-. ... .. --- -.
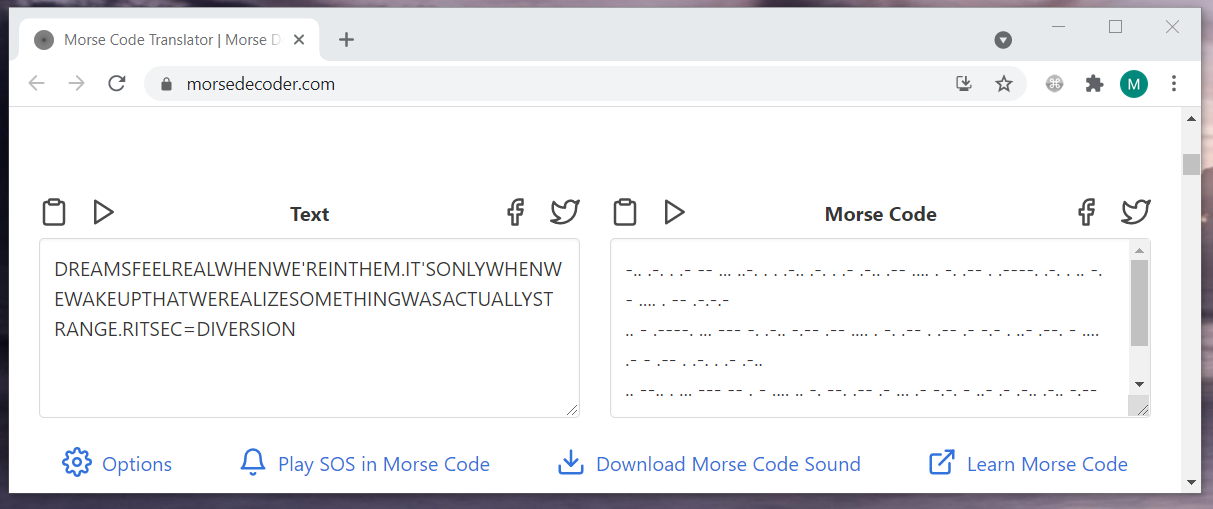
# change dir to `SnowFortress` folder
> cd SnowFortress
# extract `Limbo.7z` to `Limbo` folder using `DIVERSION` password
> 7z e Limbo.7z -oLimbo -pDIVERSION
The Limbo folder contained the final image inception.jpg.

$ strings -n10 inception.jpg
++-+-+++-+--+++-2+--77-+++-+-+---+-7+7-+7+++++7+++
6 UklUU0VDezUyODQ5MX0g
$ echo UklUU0VDezUyODQ5MX0g | base64 -d
RITSEC{528491}
I submitted the RITSEC{528491} flag for the Inception CTF: Dream 1 challenge about a dozen times. I thought it should be the correct one. Soon I realized that I have done the whole series.
- Inception CTF: Dream 1 [forensics] ~
RITSEC}Dreamland{ - Inception CTF: Dream 2 [forensics] ~
RITSEC{WaterUnderTheBridge} - Inception CTF: Dream 3 [forensics] ~
RITSEC{F@!!ingElev@tor} - Inception CTF: Dream 4 [stego] ~
RITSEC=DIVERSION - Inception CTF: Dream 5 [stego] ~
RITSEC{528491}
7. Parcel [forensics]
The challenge statement:
That’s a lot of magick
Author: knif3
File: Parcel
$ file Parcel
Parcel: gzip compressed data, from Unix, original size modulo 2^32 759456
$ gzip -d Parcel
gzip: Parcel: unknown suffix -- ignored
$ mv Parcel Parcel.gz && gzip -d Parcel.gz
$ file Parcel
Parcel: multipart/mixed; boundary="===============6501672606206171874==", ASCII text, with very long lines
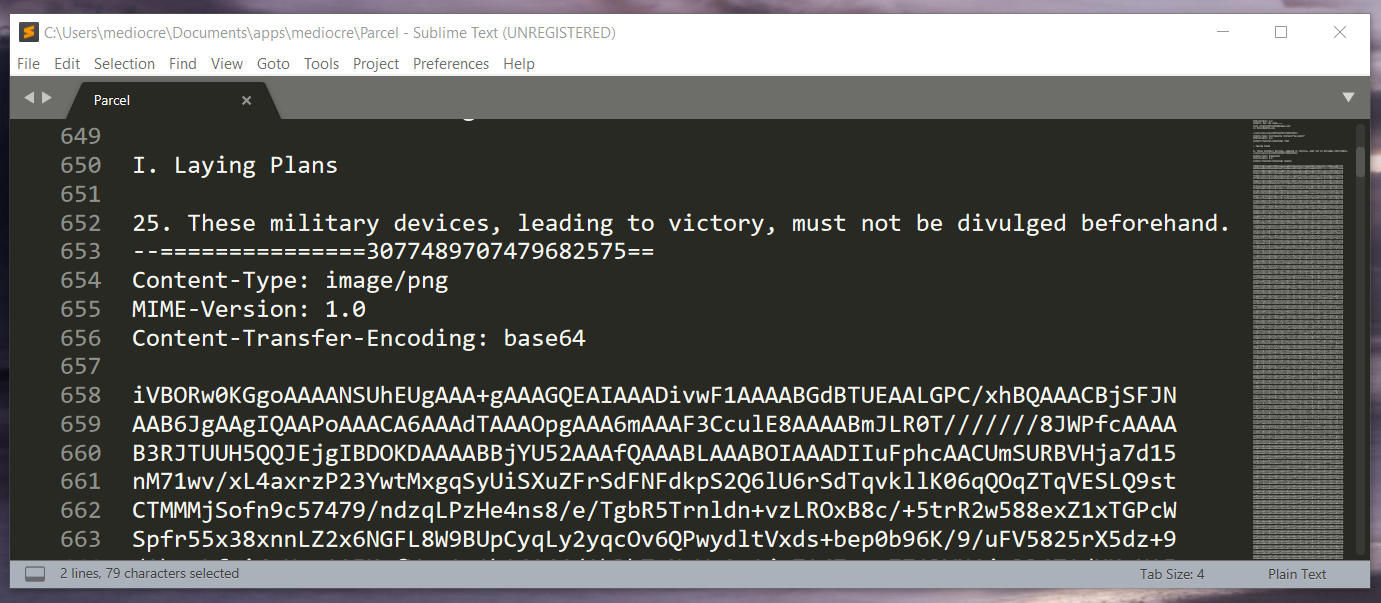
The Parcel file contained lots of base64 encoded image strings. I converted around 18 or so images using an online base64 to image service. The images in the parcel turned out to be a picture puzzle. And yet another one of my fine art piece demonstration:
8. Revision [misc]
The challenge statement:
They aren’t necessarily obvious but are helpful to know.
http://git.ritsec.club:7000/Revision.git/
Author: knif3
$ git clone http://git.ritsec.club:7000/Revision.git/
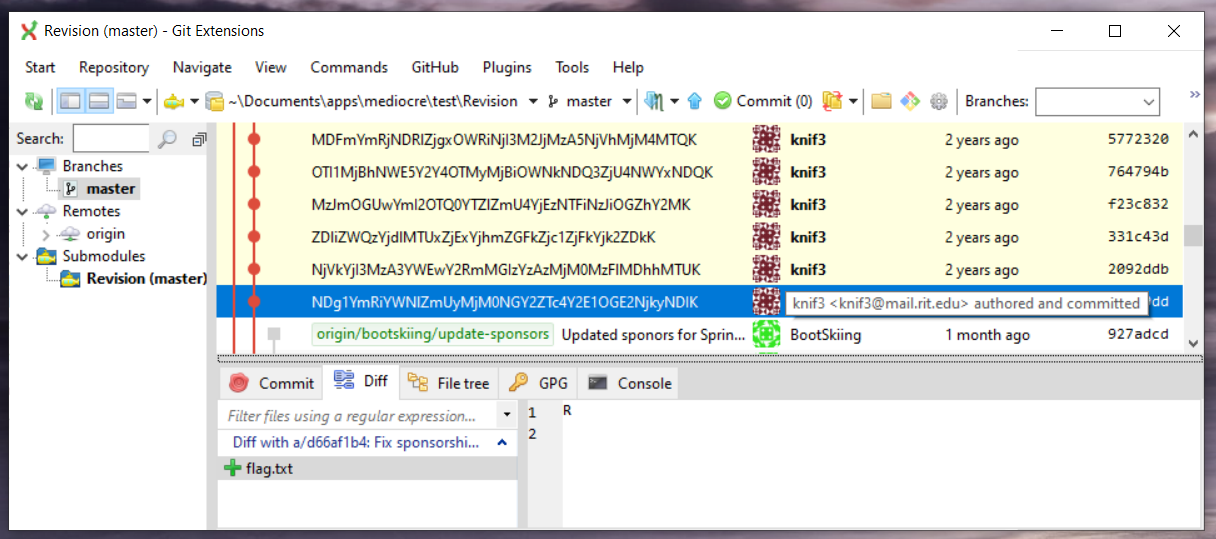
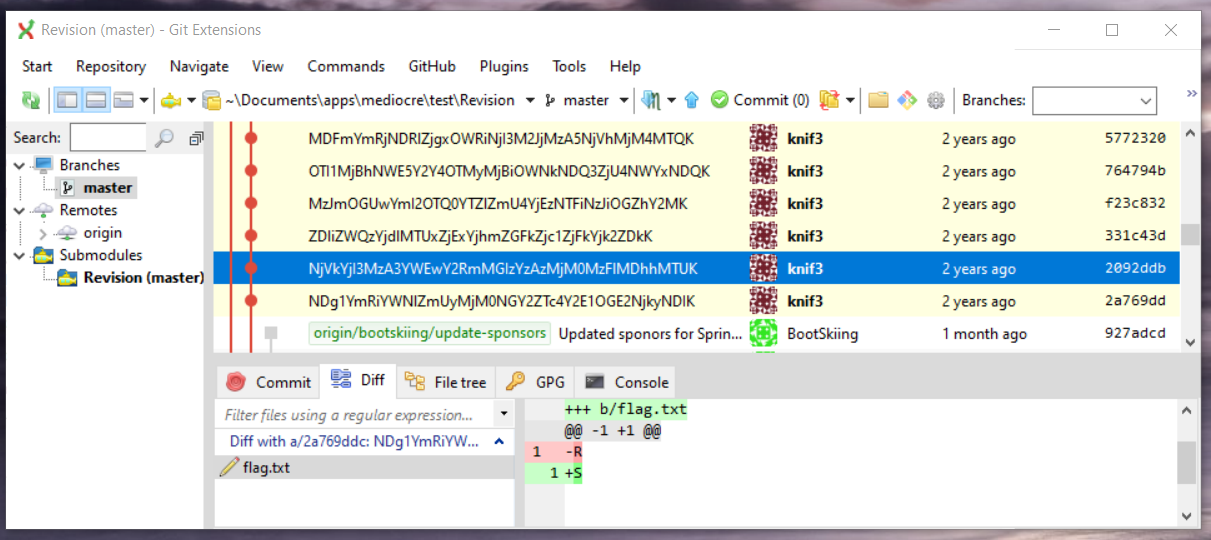
Well, we need to check the repo commit by commit for a while. That I can do :) RS{I_h0p3_y0u_scr1pted_th0s3_git_c0ms}. ~ Yeah, me too.
9. Blob [forensics]
The challenge statement:
Ha. Blob. Did you get the reference?
http://git.ritsec.club:7000/blob.git/
Author: knif3
$ git clone http://git.ritsec.club:7000/blob.git/
 I found nothing useful from the git commit history.
I found nothing useful from the git commit history.
# change dir to `blob`
$ cd blob
# list git tags
$ git tag -l
# let's see what is the `flag` tag.
$ git show flag
RS{refs_can_b3_secret_too}
10. Please Click All the Things 1: BegineersRITSEC.html [forensics]
The challenge statement:
Note: this challenge is the start of a series of challenges. The purpose of this CTF challenge is to bring real world phishing attachments to the challengers and attempt to find flags (previously executables or malicious domains) within the macros. This is often a process used in IR teams and becomes an extremely valuable skill. In this challenge we’ve brought to the table a malicious html file, GandCrab/Ursnif sample, and a IceID/Bokbot sample. We’ve rewritten the code to not contain malicious execution however system changes may still occur when executing, also some of the functionalities have been snipped and will likely not expose itself via dynamic analysis.
- Outlook helps, with proper licensing to access necessary features
- Otherwise oledump or similar would also help but isn’t necessary
- CyberChef is the ideal tool to use for decoding
Part 1: Start with the HTML file and let’s move our way up, open and or inspect the HTML file provide in the message file. There is only one flag in this document.
This challenge is brought to you by SRA
File: Please_Click_All_The_Things.7z
I was not able to download this file in my windows 10. The Microsoft Windows Defender immediately deletes my download. Congratz!
# download the file into my ubuntu box
$ wget -o check.7z https://mediocreone.com/assets/img/ritsec/Please_Click_All_The_Things.7z
# my box did not have the 7z
$ sudo apt-get install p7zip-full -y
# unzip via 7z to `check` folder
$ 7z x check.7z -ocheck
# check downloaded file
$ cd check && file Please\ Click\ all\ the\ Things.msg
Please Click all the Things.msg: CDFV2 Microsoft Outlook Message
Google: “python extract attachment from msg file” => https://pypi.org/project/extract-msg/.
# rename `Please Click all the Things` to `things` for less annoyence
$ mv Please\ Click\ all\ the\ Things.msg things.msg
# extract attachments and list folders
$ python3 -m extract_msg things.msg && ls
'2021-02-25_1658 Please Click all the Things' things.msg
# renaming the long folder name
$ mv 2021-02-25_1658\ Please\ Click\ all\ the\ Things/ things && ls things
BeginnersRITSEC.html GandCrab_Ursnif_RITSEC.docm IceID_Bokbot_RITSEC.docm message.txt
The content of the things/message.txt
From:
To: [email protected] <[email protected]>
CC:
Subject: Please Click all the Things
Date: Thu, 25 Feb 2021 16:58:00 +0000
-----------------
Hey there Challengers,
I’ve attached some malware, please do click them and infect your machines (seriously), wipe your systems after the CTF.
On a less troll note, for those new to analysis start with the HTML, move to GandCrab, and then if you’re feeling smart try IceID/Bokbot.
If you feel the need to bang your head please take safety precautions, clear away breakables including computer screens and preferably choose a softer surface to avoid injuries.
Thanks for contributing to the botnet.
Sincerely,
CTF Challenge Creators
The content of the things/BeginnersRITSEC.html
<script language="javascript">document.write(unescape('3c%68%74%6d%6c%3e%0a%3c%62%6f%64%79%3e%0a%0a%3c%21%44%4f%43%54%59%50%45%20%68%74%6d%6c%3e%0a%3c%68%74%6d%6c%3e%0a%3c%68%65%61%64%3e%0a%20%20%20%20%3c%74%69%74%6c%65%3e%49%74%73%20%6a%75%73%74%20%61%6e%6f%74%68%65%72%20%66%72%69%65%6e%64%6c%79%20%66%69%6c%65%20%66%72%6f%6d%20%79%6f%75%27%72%65%20%6c%6f%63%61%6c%20%43%54%46%3c%2f%74%69%74%6c%65%3e%0a%20%20%20%20%3c%73%74%79%6c%65%20%74%79%70%65%3d%22%74%65%78%74%2f%63%73%73%22%3e%0a%20%20%20%20%20%20%20%20%68%74%6d%6c%20%7b%0a%20%20%20%20%20%20%20%20%20%20%20%20%68%65%69%67%68%74%3a%20%31%30%30%25%3b%0a%20%20%20%20%20%20%20%20%20%20%20%20%77%69%64%74%68%3a%20%31%30%30%25%3b%0a%20%20%20%20%20%20%20%20%7d%0a%0a%20%20%20%20%20%20%20%20%23%66%65%61%74%75%72%65%20%7b%0a%20%20%20%20%20%20%20%20%20%20%20%20%77%69%64%74%68%3a%20%39%38%30%70%78%3b%0a%20%20%20%20%20%20%20%20%20%20%20%20%6d%61%72%67%69%6e%3a%20%39%35%70%78%20%61%75%74%6f%20%30%20%61%75%74%6f%3b%0a%20%20%20%20%20%20%20%20%20%20%20%20%6f%76%65%72%66%6c%6f%77%3a%20%61%75%74%6f%3b%0a%20%20%20%20%20%20%20%20%7d%0a%0a%20%20%20%20%20%20%20%20%23%63%6f%6e%74%65%6e%74%20%7b%0a%20%20%20%20%20%20%20%20%20%20%20%20%66%6f%6e%74%2d%66%61%6d%69%6c%79%3a%20%22%53%65%67%6f%65%20%55%49%22%3b%0a%20%20%20%20%20%20%20%20%20%20%20%20%66%6f%6e%74%2d%77%65%69%67%68%74%3a%20%6e%6f%72%6d%61%6c%3b%0a%20%20%20%20%20%20%20%20%20%20%20%20%66%6f%6e%74%2d%73%69%7a%65%3a%20%32%32%70%78%3b%0a%20%20%20%20%20%20%20%20%20%20%20%20%63%6f%6c%6f%72%3a%20%23%66%66%66%66%66%66%3b%0a%20%20%20%20%20%20%20%20%20%20%20%20%66%6c%6f%61%74%3a%20%6c%65%66%74%3b%0a%20%20%20%20%20%20%20%20%20%20%20%20%77%69%64%74%68%3a%20%34%36%30%70%78%3b%0a%20%20%20%20%20%20%20%20%20%20%20%20%6d%61%72%67%69%6e%2d%74%6f%70%3a%20%36%38%70%78%3b%0a%20%20%20%20%20%20%20%20%20%20%20%20%6d%61%72%67%69%6e%2d%6c%65%66%74%3a%20%30%70%78%3b%0a%20%20%20%20%20%20%20%20%20%20%20%20%76%65%72%74%69%63%61%6c%2d%61%6c%69%67%6e%3a%20%6d%69%64%64%6c%65%3b%0a%20%20%20%20%20%20%20%20%7d%0a%0a%20%20%20%20%20%20%20%20%20%20%20%20%23%63%6f%6e%74%65%6e%74%20%68%31%20%7b%0a%20%20%20%20%20%20%20%20%20%20%20%20%20%20%20%20%66%6f%6e%74%2d%66%61%6d%69%6c%79%3a%20%22%53%65%67%6f%65%20%55%49%20%4c%69%67%68%74%22%3b%0a%20%20%20%20%20%20%20%20%20%20%20%20%20%20%20%20%63%6f%6c%6f%72%3a%20%23%66%66%66%66%66%66%3b%0a%20%20%20%20%20%20%20%20%20%20%20%20%20%20%20%20%66%6f%6e%74%2d%77%65%69%67%68%74%3a%20%6e%6f%72%6d%61%6c%3b%0a%20%20%20%20%20%20%20%20%20%20%20%20%20%20%20%20%66%6f%6e%74%2d%73%69%7a%65%3a%20%36%30%70%78%3b%0a%20%20%20%20%20%20%20%20%20%20%20%20%20%20%20%20%6c%69%6e%65%2d%68%65%69%67%68%74%3a%20%34%38%70%74%3b%0a%20%20%20%20%20%20%20%20%20%20%20%20%20%20%20%20%77%69%64%74%68%3a%20%39%38%30%70%78%3b%0a%20%20%20%20%20%20%20%20%20%20%20%20%7d%0a%0a%20%20%20%20%20%20%20%20%70%20%61%2c%20%70%20%61%3a%76%69%73%69%74%65%64%2c%20%70%20%61%3a%61%63%74%69%76%65%2c%20%70%20%61%3a%68%6f%76%65%72%20%7b%0a%20%20%20%20%20%20%20%20%20%20%20%20%63%6f%6c%6f%72%3a%20%23%66%66%66%66%66%66%3b%0a%20%20%20%20%20%20%20%20%7d%0a%0a%20%20%20%20%20%20%20%20%23%63%6f%6e%74%65%6e%74%20%61%2e%62%75%74%74%6f%6e%20%7b%0a%20%20%20%20%20%20%20%20%20%20%20%20%62%61%63%6b%67%72%6f%75%6e%64%3a%20%23%30%44%42%43%46%32%3b%0a%20%20%20%20%20%20%20%20%20%20%20%20%62%6f%72%64%65%72%3a%20%31%70%78%20%73%6f%6c%69%64%20%23%46%46%46%46%46%46%3b%0a%20%20%20%20%20%20%20%20%20%20%20%20%63%6f%6c%6f%72%3a%20%23%46%46%46%46%46%46%3b%0a%20%20%20%20%20%20%20%20%20%20%20%20%64%69%73%70%6c%61%79%3a%20%69%6e%6c%69%6e%65%2d%62%6c%6f%63%6b%3b%0a%20%20%20%20%20%20%20%20%20%20%20%20%66%6f%6e%74%2d%66%61%6d%69%6c%79%3a%20%53%65%67%6f%65%20%55%49%3b%0a%20%20%20%20%20%20%20%20%20%20%20%20%66%6f%6e%74%2d%73%69%7a%65%3a%20%32%34%70%78%3b%0a%20%20%20%20%20%20%20%20%20%20%20%20%6c%69%6e%65%2d%68%65%69%67%68%74%3a%20%34%36%70%78%3b%0a%20%20%20%20%20%20%20%20%20%20%20%20%6d%61%72%67%69%6e%2d%74%6f%70%3a%20%31%30%70%78%3b%0a%20%20%20%20%20%20%20%20%20%20%20%20%70%61%64%64%69%6e%67%3a%20%30%20%31%35%70%78%20%33%70%78%3b%0a%20%20%20%20%20%20%20%20%20%20%20%20%74%65%78%74%2d%64%65%63%6f%72%61%74%69%6f%6e%3a%20%6e%6f%6e%65%3b%0a%20%20%20%20%20%20%20%20%7d%0a%0a%20%20%20%20%20%20%20%20%20%20%20%20%23%63%6f%6e%74%65%6e%74%20%61%2e%62%75%74%74%6f%6e%20%69%6d%67%20%7b%0a%20%20%20%20%20%20%20%20%20%20%20%20%20%20%20%20%66%6c%6f%61%74%3a%20%72%69%67%68%74%3b%0a%20%20%20%20%20%20%20%20%20%20%20%20%20%20%20%20%70%61%64%64%69%6e%67%3a%20%31%30%70%78%20%30%20%30%20%31%35%70%78%3b%0a%20%20%20%20%20%20%20%20%20%20%20%20%7d%0a%0a%20%20%20%20%20%20%20%20%20%20%20%20%23%63%6f%6e%74%65%6e%74%20%61%2e%62%75%74%74%6f%6e%3a%68%6f%76%65%72%20%7b%0a%20%20%20%20%20%20%20%20%20%20%20%20%20%20%20%20%62%61%63%6b%67%72%6f%75%6e%64%3a%20%23%31%43%37%35%42%43%3b%0a%20%20%20%20%20%20%20%20%20%20%20%20%7d%0a%0a%2f%2a%20%6c%6f%61%64%69%6e%67%20%64%6f%74%73%20%2a%2f%0a%0a%2e%6c%6f%61%64%69%6e%67%3a%61%66%74%65%72%20%7b%0a%20%20%63%6f%6e%74%65%6e%74%3a%20%27%2e%27%3b%0a%20%20%61%6e%69%6d%61%74%69%6f%6e%3a%20%64%6f%74%73%20%31%73%20%73%74%65%70%73%28%35%2c%20%65%6e%64%29%20%69%6e%66%69%6e%69%74%65%7d%0a%0a%40%6b%65%79%66%72%61%6d%65%73%20%64%6f%74%73%20%7b%0a%20%20%30%25%2c%20%32%30%25%20%7b%0a%20%20%20%20%63%6f%6c%6f%72%3a%20%72%67%62%61%28%30%2c%30%2c%30%2c%30%29%3b%0a%20%20%20%20%74%65%78%74%2d%73%68%61%64%6f%77%3a%0a%20%20%20%20%20%20%2e%32%35%65%6d%20%30%20%30%20%72%67%62%61%28%30%2c%30%2c%30%2c%30%29%2c%0a%20%20%20%20%20%20%2e%35%65%6d%20%30%20%30%20%72%67%62%61%28%30%2c%30%2c%30%2c%30%29%3b%7d%0a%20%20%34%30%25%20%7b%0a%20%20%20%20%63%6f%6c%6f%72%3a%20%77%68%69%74%65%3b%0a%20%20%20%20%74%65%78%74%2d%73%68%61%64%6f%77%3a%0a%20%20%20%20%20%20%2e%32%35%65%6d%20%30%20%30%20%72%67%62%61%28%30%2c%30%2c%30%2c%30%29%2c%0a%20%20%20%20%20%20%2e%35%65%6d%20%30%20%30%20%72%67%62%61%28%30%2c%30%2c%30%2c%30%29%3b%7d%0a%20%20%36%30%25%20%7b%0a%20%20%20%20%74%65%78%74%2d%73%68%61%64%6f%77%3a%0a%20%20%20%20%20%20%2e%32%35%65%6d%20%30%20%30%20%77%68%69%74%65%2c%0a%20%20%20%20%20%20%2e%35%65%6d%20%30%20%30%20%72%67%62%61%28%30%2c%30%2c%30%2c%30%29%3b%7d%0a%20%20%38%30%25%2c%20%31%30%30%25%20%7b%0a%20%20%20%20%74%65%78%74%2d%73%68%61%64%6f%77%3a%0a%20%20%20%20%20%20%2e%32%35%65%6d%20%30%20%30%20%77%68%69%74%65%2c%0a%20%20%20%20%20%20%2e%35%65%6d%20%30%20%30%20%77%68%69%74%65%3b%7d%7d%0a%20%20%20%20%3c%2f%73%74%79%6c%65%3e%0a%3c%2f%68%65%61%64%3e%0a%3c%62%6f%64%79%20%62%67%63%6f%6c%6f%72%3d%22%23%30%30%61%62%65%63%22%3e%0a%20%20%20%20%3c%64%69%76%20%69%64%3d%22%66%65%61%74%75%72%65%22%3e%0a%20%20%20%20%20%20%20%20%20%20%20%20%3c%64%69%76%20%69%64%3d%22%63%6f%6e%74%65%6e%74%22%3e%0a%20%20%20%20%20%20%20%20%20%20%20%20%20%20%20%20%3c%68%31%20%69%64%3d%22%75%6e%61%76%61%69%6c%61%62%6c%65%22%20%63%6c%61%73%73%3d%22%6c%6f%61%64%69%6e%67%22%3e%54%72%79%20%48%61%72%64%65%72%3c%2f%68%31%3e%0a%20%20%20%20%20%20%20%20%20%20%20%20%20%20%20%20%3c%70%20%69%64%3d%22%74%72%79%41%67%61%69%6e%22%20%63%6c%61%73%73%3d%22%6c%6f%61%64%69%6e%67%22%3e%54%68%65%20%44%65%66%65%6e%64%65%72%20%54%68%61%74%20%43%6f%75%6c%64%3c%2f%70%3e%0a%20%20%20%20%20%20%20%20%3c%2f%64%69%76%3e%0a%20%20%20%20%3c%2f%64%69%76%3e%0a%3c%2f%62%6f%64%79%3e%0a%0a%0a%20%20%3c%68%65%61%64%3e%20%0a%3c%66%6c%61%67%3d%22%55%6b%6c%55%55%30%56%44%65%30%67%7a%63%6a%4d%68%64%43%45%6b%66%51%3d%3d%22%3e%0a%3c%2f%62%6f%64%79%3e%0a%20%20%3c%2f%68%74%6d%6c%3e'));</script>
The content after decoding it with an online URL decoding service.
3chtml>
<body>
<!DOCTYPE html>
<html>
<head>
<title>Its just another friendly file from you're local CTF</title>
<style type="text/css">
/* MediocreOne note: deleted CSS rules to make life easier */
</style>
</head>
<body bgcolor="#00abec">
<div id="feature">
<div id="content">
<h1 id="unavailable" class="loading">Try Harder</h1>
<p id="tryAgain" class="loading">The Defender That Could</p>
</div>
</div>
</body>
<head>
<flag="UklUU0VDe0gzcjMhdCEkfQ==">
</body>
</html>
echo UklUU0VDe0gzcjMhdCEkfQ== | base64 -d
RITSEC{H3r3!t!$}
11. Please Click All the Things 2: GandCrab_Ursnif.html [forensics]
The challenge statement:
GandCrab/Ursnif are dangerous types of campaigns and malware, macros are usually the entry point,
see what you can find, there are two flags in this document. Flag1/2
Author: Brandon Martin
- Google: “python extract macros from dotm” => https://blog.didierstevens.com/programs/oledump-py/
- Google: “Github oledump” => https://github.com/DidierStevens/DidierStevensSuite/blob/master/oledump.py
# change dir to `things` folder
$ cd things
# download the `oledump.py`
wget https://raw.githubusercontent.com/DidierStevens/DidierStevensSuite/master/oledump.py
# analyze the `GandCrab_Ursnif_RITSEC.docm` file
$ python3 oledump.py GandCrab_Ursnif_RITSEC.docm
A: word/vbaProject.bin
A1: 464 'PROJECT'
A2: 89 'PROJECTwm'
A3: M 975 'VBA/Module1'
A4: M 1504 'VBA/Module4'
A5: m 938 'VBA/ThisDocument'
A6: 3109 'VBA/_VBA_PROJECT'
A7: 585 'VBA/dir'
# dump macro at A3
$ python3 oledump.py -s A3 -v GandCrab_Ursnif_RITSEC.docm
Attribute VB_Name = "Module1"
Sub autoopen()
TheDarkSide
End Sub
# dump macro at A4
$ python3 oledump.py -s A4 -v GandCrab_Ursnif_RITSEC.docm
Attribute VB_Name = "Module4"
Function TheDarkSide()
On Error Resume Next
CTF = Array(ElonMusk, StarWars, HelloWorld, Interaction.Shell(CleanString(Chewbacca.TextBox1), 43 - 43), Mars)
Select Case Research
Case 235003991
CompetitorSkillz = That_of_a_Storm_Troopers_Aim_Research_Pending
Flag = RITSEC{M@CROS}
PendingResearch = Oct(Date + CStr(TimeStamp + Log(241371097) - PewPew / Hex(13775121)))
End Select
End Function
At least we seem to land on our first flag RITSEC{M@CROS}.
12. Please Click All the Things 3: IceID [forensics]
The challenge statement:
Stepping it up to IceID/Bokbot, this challenge is like the previous challenge but requires some ability to read and understand coding in addition to some additional decoding skills, there are two flags in this document. (Flag 1/2)
Author: Brandon Martin
# analyze the `IceID_Bokbot_RITSEC.docm` file
$ python3 oledump.py IceID_Bokbot_RITSEC.docm
A: word/vbaProject.bin
A1: 631 'PROJECT'
A2: 149 'PROJECTwm'
A3: 97 'UserForm1/\x01CompObj'
A4: 292 'UserForm1/\x03VBFrame'
A5: 90 'UserForm1/f'
A6: 72 'UserForm1/o'
A7: M 3460 'VBA/Module1'
A8: M 1159 'VBA/Module2'
A9: M 1622 'VBA/NewMacros'
A10: m 938 'VBA/ThisDocument'
A11: M 1571 'VBA/UserForm1'
A12: 4182 'VBA/_VBA_PROJECT'
A13: 926 'VBA/dir'
# dump macro at A7
$ python3 oledump.py -s A7 -v IceID_Bokbot_RITSEC.docm
Attribute VB_Name = "Module1"
Public Const aHVWt As String = "p_:_\_j_v_a_q_b_j_f_\_f_l_f_g_r_z_3_2_\_z_f_u_g_n__r_k_r_"
Public Const aqv6tf As String = "EVGFRP{E0GG1ATZ@YP0Q3}"
Public Const a7sVN As String = "_"
Public Const asXlUN As Integer = -954 + 967
Public Function aENoBO(aHu95, avuEG8)
FileNumber = FreeFile
Open aHu95 For Output As #FileNumber
Print #FileNumber, Spc(-413 + 456)
Print #FileNumber, avuEG8
Print #FileNumber, Spc(-413 + 456)
Close #FileNumber
End Function
Sub aUoaN(adDgz, at09Aq)
FileCopy adDgz, at09Aq
End Sub
Function anPr56(aCl8i)
anPr56 = Len(aCl8i)
End Function
Function a79yA(aO0h5k)
a79yA = aO0h5k + 12324 / 474
End Function
Function aHScDO(aoza8) As String
Dim alc6yS As Long
Dim a9uRX As Integer
Dim agyvb As Integer
For alc6yS = 1 To anPr56(aoza8)
agyvb = 0
aFxdHY = VBA.Mid$(aoza8, alc6yS, 1)
a9uRX = Asc(aFxdHY)
If (a9uRX > 64 And a9uRX < 91) Or (a9uRX > 96 And a9uRX < 123) Then
agyvb = asXlUN
a9uRX = a9uRX - agyvb
If a9uRX < 97 And a9uRX > 83 Then
a9uRX = a79yA(a9uRX)
ElseIf a9uRX < 65 Then
a9uRX = a79yA(a9uRX)
End If
End If
Mid$(aoza8, alc6yS, 1) = VBA.Chr$(a9uRX)
Next
aHScDO = aoza8
End Function
From here, the string EVGFRP{E0GG1ATZ@YP0Q3} looked awfully like a flag. I tried a couple of websites and eventually found the correct one.
Well, there were a lot of cool challenges in this CTF. Those that I spent the most time and did not manage to solve taught me a lot. Thanks to those who organized the event.